IT audit services in Kazakhstan
The rapid automation of aging work methods significantly increases the value of information technology for almost any type of business. Information has become a new kind of financial assets that require proper management. Timely and qualified response to the constantly changing IT and IS landscape will prevent both direct losses associated with compromised information systems and indirect ones appearing as a form of costs to eliminate security gaps, possible fines by regulators or due to property penalties by court decision.
The international team of experts with many years of experience in the field of practical information security and information technology management will provide an integrated approach to the issues of independent assessment of the effectiveness and security of information technology. IT audit and information security services are provided throughout Central Asia: in Kazakhstan, the Kyrgyz Republic, Uzbekistan, Tajikistan and Turkmenistan. The result of our work is a description of identified inconsistencies, a detailed methodology and evidence of their detection, as well as qualified recommendations for eliminating identified risks. The main objective is the unbiased determination and professional adjustment of the specific information security management process, which allows the formation of vulnerabilities or inconsistencies.
IT audit results
The results of the IT audit, presented in the form of a signed report with an independent audit conclusion, provide an objective assessment of the current state of the IT infrastructure, systems, as well as the effectiveness of staff actions and the valid IT and IS management processes.
A visual representation of the identified vulnerabilities having no compliance with applicable requirements and audit criteria is accompanied by a description of the collected evidences that allows them to be reproduced. The report includes a risk assessment for each of the inconsistencies with conclusions about the likelihood of consequences and an assessment of the estimated damage that may occur as a result of the most negative development way.
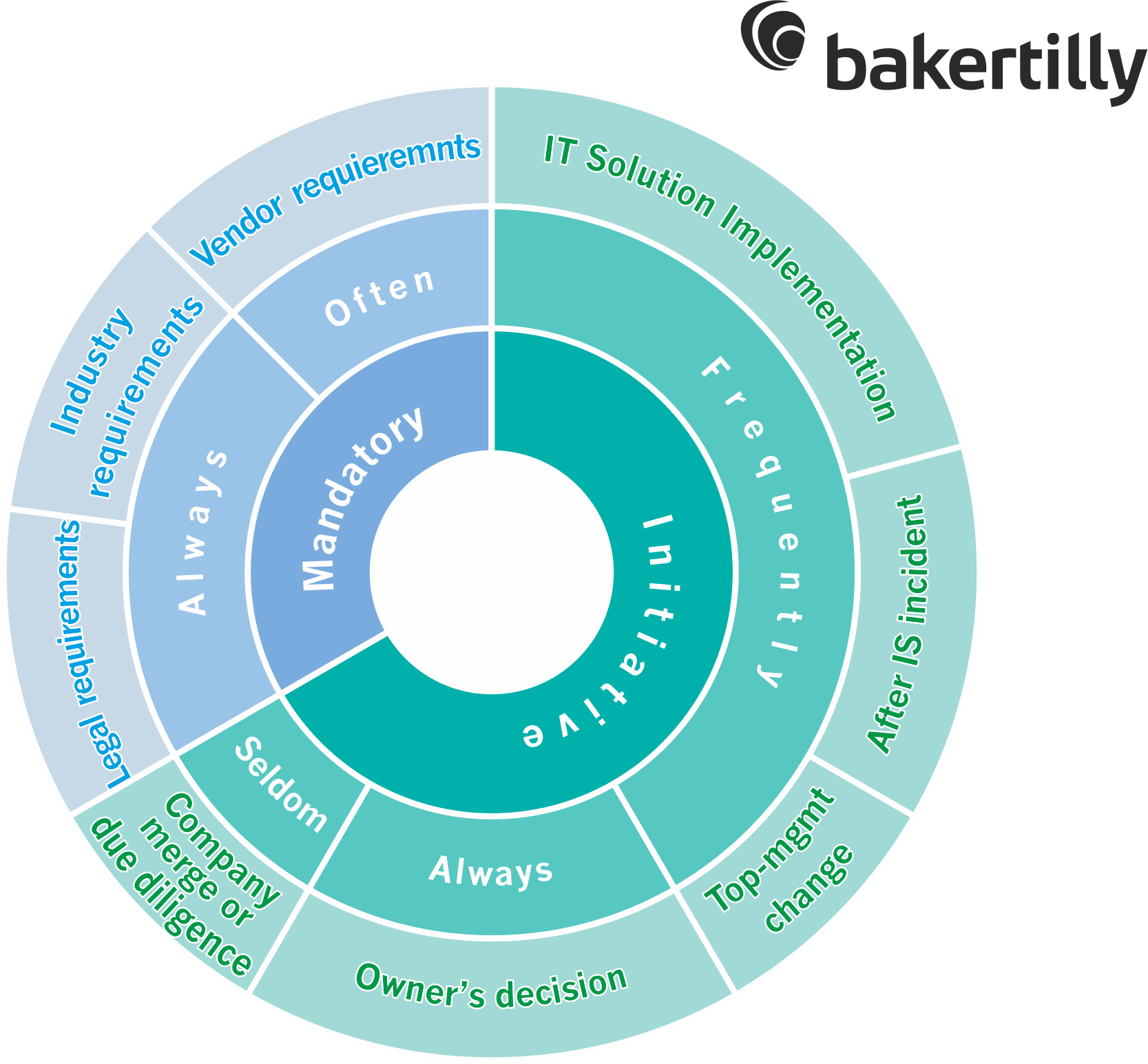
IT audit results application
According to the established practice, linear IT / IS managers and top management of the organization use the results of the audit to take concrete actions to improve the existing processes and implement relevant ones in the field of IT and IB management, for example:
- personnel assessment allows you to identify high-risk areas associated with the human factor, and carry out the reorganization of processes in such a way as to minimize or completely eliminate the risks;
- the register of the identified inconsistencies, deficiencies or vulnerabilities is a list of key zones, processes and systems with specific flaws, and recommended ways to remedy them;
- ways and means of risks minimization, expressed in the form of recommendations, allow to identify implicit risks and include them into existing risk management methodologies for drawing up an action plan to reduce risks up to an acceptable level;
- justification of the cost of purchasing or upgrading equipment and software often stems from the conclusions and recommendations set out in the report, which allows you to direct the vector of budget planning in IT and IS departments towards improving the efficiency of specific infrastructure components;
- justification of investment in training is a likely consequence of the results of the personnel assessment and a confirmed independent assessment of the need for regular professional development as one of the important factors for managing information security processes;
- TCO (Total Cost of Ownership) management allows you to define the boundaries of the effectiveness of IT solutions, taking into account objective capital costs, as well as direct and indirect operating costs arising from information security incidents;
- effective use of systems is a direct consequence of compliance with the recommendations in the audit report.

Our IT audit and information security specialists have received professional industry training at leading educational institutions:
- Texas A&M University TAMU (Texas, USA),
- Federal Institute of Emergency Management and Critical Infrastructure Protection (FEMA) of US Homeland Security Dept,
- Ethical Hacking Academy (EH Academy, Oregon, USA).
Leading Baker Tilly experts are members of industry and professioanl associations:
- Institute of Internal Auditors (IIA, Moscow Charter),
- SUDEX, the Chamber of Forensic experts in the field of computer forensics 21.1RU
Our experts hold world-class certifications in the following fields of expertise
- information security risk management specialist,
- specialist in protection of critical information infrastructure,
- Lead auditor of information security management systems ISO27001,
- ISACA CISA Certification Training Program as Certified Information System Auditor,
- Red Hat Certified Engineer (RHCE)
- and other industry certifications.
Baker Tilly has been a Kaspersky Lab partner in information security incident response and management since 2017.
IT audit and information security assessment services in the Kyrgyz Republic comply with all national requirements, interstate agreements and international standards.